Posted In: Health Care
Industry:
Health Care
Compliance Checkup: Mastering HIPAA: Part 2 - Analyze First, Panic Second
on April 9, 2019
What would you do if your practice changed locations and an employee accidentally left boxes of paper medical records at the old location? You might panic at first, but this Compliance Checkup is a reminder to approach any potential Health Insurance Portability and Accountability Act (HIPAA) breach as just that - a potential breach. The fine folks at the Centers for Medicare and Medicaid Services (CMS) have given us a risk analysis tool at 45 CFR 164.402 so that you can make a critical assessment to determine whether a breach has actually occurred or whether there is a low probability that the patient information has been compromised.
This multi-factor risk assessment must consider, at a minimum, the following:
- The nature and extent of the Protected Health Information (PHI) involved, including the types of identifiers and the likelihood of re-identification;
- The unauthorized person who used the PHI or to whom the disclosure was made;
- Whether the PHI was actually acquired or viewed; and
- The extent to which the risk to the PHI has been mitigated.
Here is a handy flow chart of the risk analysis tool:
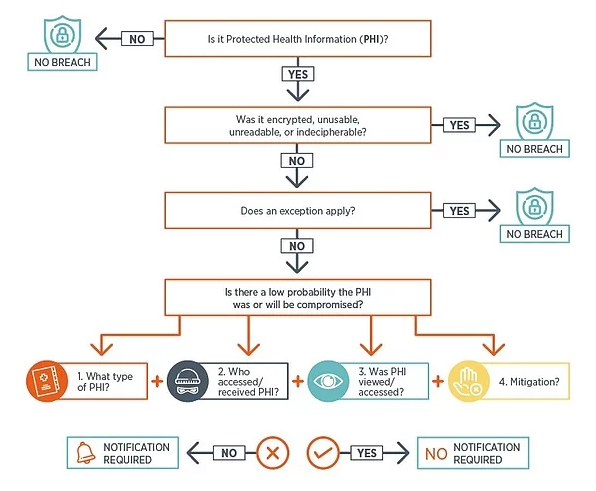
After you have gathered all of the facts about the potential breach, use this tool to assess whether a breach has actually occurred. It’s easy to assume the worst, but you’ll want to make sure you have analyzed a breach thoroughly before you decide to report a breach. Regarding the example about the missing boxes above, you may discover that you can easily retrieve the boxes from your former practice location before anyone discovers them, or another covered entity moved into the space and has held the records in a safe place.
Consider all of the factors in combination and evaluate the overall probability that PHI has been compromised. If, as a result of this risk assessment, you cannot demonstrate that there is low probability that PHI has been compromised, you must follow the breach notification process. However, if you reach a reasonable conclusion PHI has not been compromised, breach notification is not required.
This blog is intended to provide information generally and to identify general legal requirements. It is not intended as a form of, or as a substitute for legal advice. Such advice should always come from in-house or retained counsel. Moreover, if this Blog in any way seems to contradict advice of counsel, counsel's opinion should control over anything written herein. No attorney client relationship is created or implied by this Blog. © 2024 Brouse McDowell. All rights reserved.






